How to Secure IT Operations with Netmaker
This document explains how to use Netmaker to secure IT operations with private, encrypted networks, covering traffic control, scalability, and zero-trust best practices for cloud, on-prem, and hybrid infrastructures.
This guide explains how to securely access resources at remote sites, which is particularly useful for organizations with employees working from home, in the field, or traveling. It is also beneficial for situations where in-office employees need to securely connect to company resources from different locations, such as a server at a production site in another state or country. In our example scenario, we demonstrate how users can securely access critical resources located at remote sites, ensuring reliable and protected connectivity across various locations.
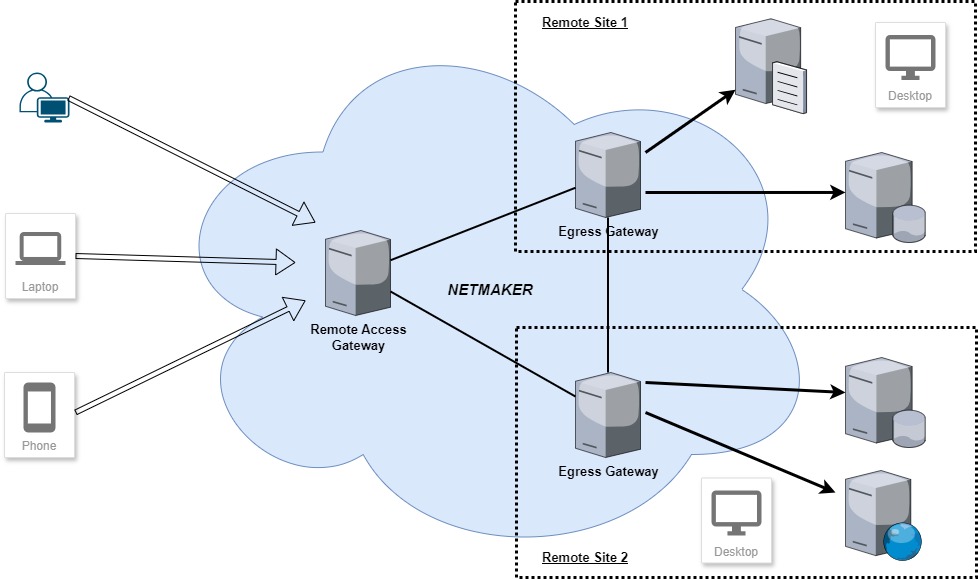
As illustrated in the diagram, users initiate access through the Remote Access Gateway (RAGw), which is part of the Netmaker network. The RAGw then routes this traffic to Egress Gateways—machines that are both part of their respective remote site networks and the Netmaker network. In this scenario, the Egress Gateways operate behind NAT routers.
This tunnel connection provides end-users with encrypted access to remote site resources, such as intranet servers or file servers, ensuring secure and seamless communication between the user and the remote network.
Prerequisites
Access to a running Netmaker server, either self-hosted or hosted in the cloud (SaaS).
A Linux machine at the remote location.
Access to the router at the remote location, or at least sufficient access to add a Port Forwarding rule.
OAuth integrated on the Netmaker server (refer here for more information: Integrating OAuth)
General Steps
Plan your network
Ensure the remote sites, the Netmaker network, and optionally the end-user network do not have overlapping address ranges. Overlaps can cause traffic to prefer directly connected devices rather than the intended remote resources.
Example address spaces used in this guide:
Netmaker network: 100.100.0.0/16
Remote Site: 192.168.254.0/24
User network: 192.168.111.0/24
Network name used in this guide: "my-org-vpn".
For detailed instructions on creating a VPN network in Netmaker, see: Create Networks.
Set up remote access with a Remote Access Gateway
A Remote Access Gateway (Ingress Gateway) should be publicly reachable. The Netmaker server or Managed Endpoint (SaaS) can act as the RAGw, or you can add a separate machine.
To join a machine to the Netmaker VPN: see Add Non-User Devices. To assign a machine as a Remote Access Gateway: see Configuring a Remote Access Gateway.
Only UDP port 51821 needs to be exposed for Netclient communication.
Ubuntu example (UFW):
You can use nftables as a replacement if you're using Linux machines that have deprecated iptables.

Set up Egress Gateways
Egress Gateways are Linux machines running Netclient on the remote site's network that expose internal routes into the Netmaker VPN.
To join machines to the Netmaker VPN: see Add Non-User Devices. Only UDP port 51821 needs to be exposed as with RAGw.
Steps to create and configure an Egress Gateway in the Netmaker UI:
Add external routes
Under the Egress Gateways table, click the newly created host.
Click the “Add external route” button.
In the Update Egress modal, click “Add range”.
To expose an entire LAN, specify the network (e.g., 192.168.254.0/24). To expose specific hosts, use individual addresses (for example 192.168.254.3/32).

If the Egress Gateway is behind NAT, set a static listening port for that host to avoid relays or unexpected UDP port changes:
Login to the Netmaker server.
Navigate to Hosts, find the Egress Gateway host, hover the kebab icon and click Edit Host.
Enable the Static Port switch.
Click Update Device.

Add port forwarding rules on the remote site's router
Routers frequently block unsolicited inbound traffic. Add a port forwarding rule for UDP 51821 to the Egress Gateway private IP to allow encrypted VPN traffic into the private network.
Example on a Mikrotik router (web UI):
IP => Firewall => NAT => Add New
In Action, set “To Addresses” to the Egress Gateway private IP.
Apply and OK.
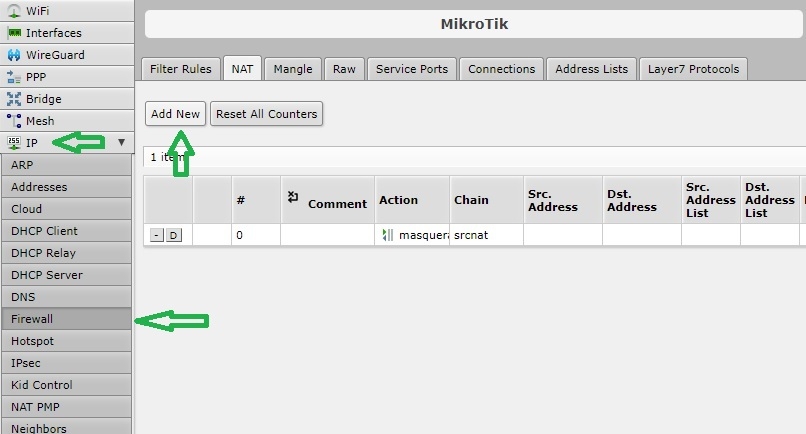
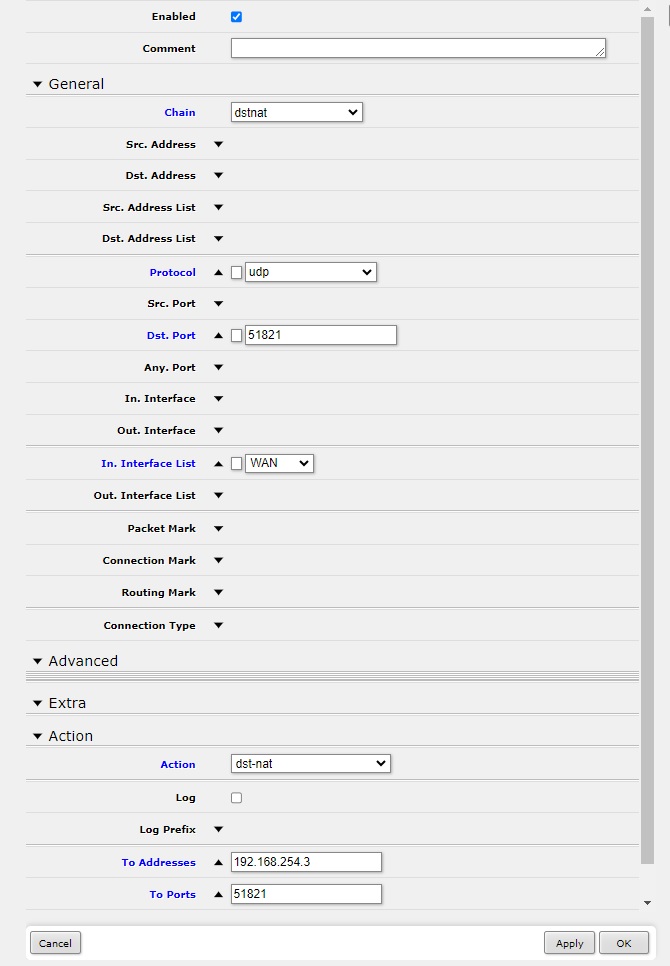
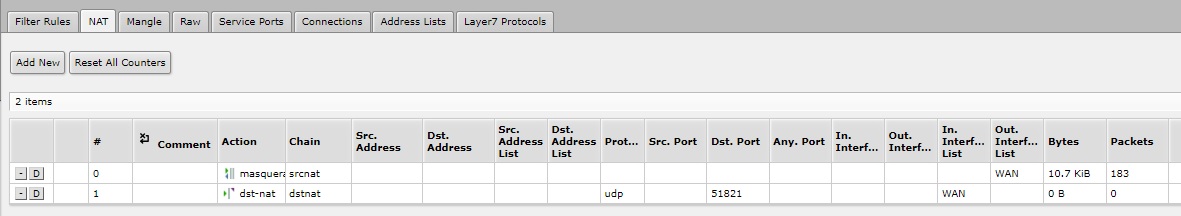
Please refer to your router’s documentation for specific instructions.
Onboard users
Provide users with access via one of these methods:
Give users credentials (Basic Auth) — Self-hosted only.
Send invites (email) — requires SMTP on Self-hosted, or available on SaaS.
Let users sign up themselves using OAuth/SSO.
Refer to User Management.
We demonstrate assigning the Service User role. Service Users use the Remote Access Client (RAC) to log in; this is preferred to sharing config files.
Setup Remote Access Gateway
(Section moved under General Steps for flow; see that step for UFW commands and notes.)
Setup Egress Gateways
(Section moved under General Steps for flow; see that step for UI workflow and static port configuration.)
Onboarding Users — Methods and UI Steps
Giving users their login credentials (Basic Auth — Self-hosted)

Instruct users to download and run the Remote Access Client (RAC) and log in with the provided username/password.
Inviting Service Users (email invites)
This method uses email addresses as usernames. Users set their own password or use SSO. Invites are sent via email.
Note: SMTP configuration is required for Self-hosted Netmaker. SaaS Netmaker has SMTP configured.
Setting up SMTP (Self-hosted)
Use an SMTP provider (example: Gmail app password via https://myaccount.google.com/apppasswords). Configure in Netmaker Dashboard → Settings → Email Configuration.

Invite flow
Login to the Netmaker Server UI.
Navigate to User Management.
Hover Add a User and click Invite User.
Specify email(s), tick Service User.
Under Additional Roles Per Network, for “my-org-vpn” select the Remote Access Gateway host.
Click Create User Invite(s), then Finish.

You can invite multiple emails separated by commas (no spaces needed). Ask users to check their email and use the invitation link.
End-user signup via invite link
Users follow the invite link and can sign up using SSO (Google, Microsoft, GitHub) or provide their own password. The chosen method is what they will use with RAC.
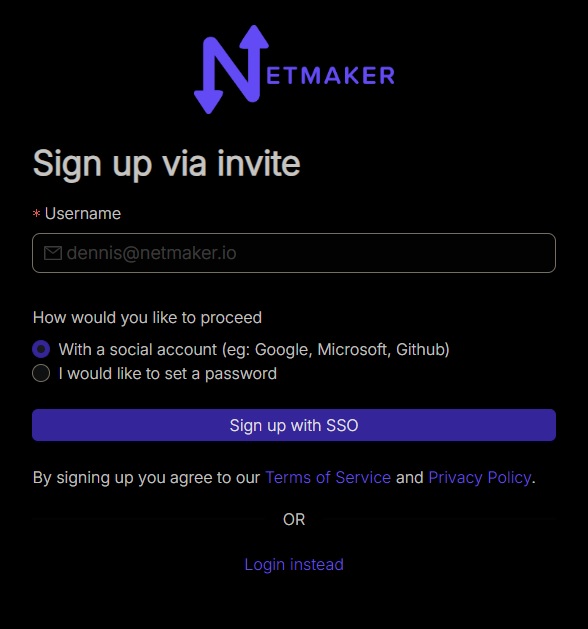
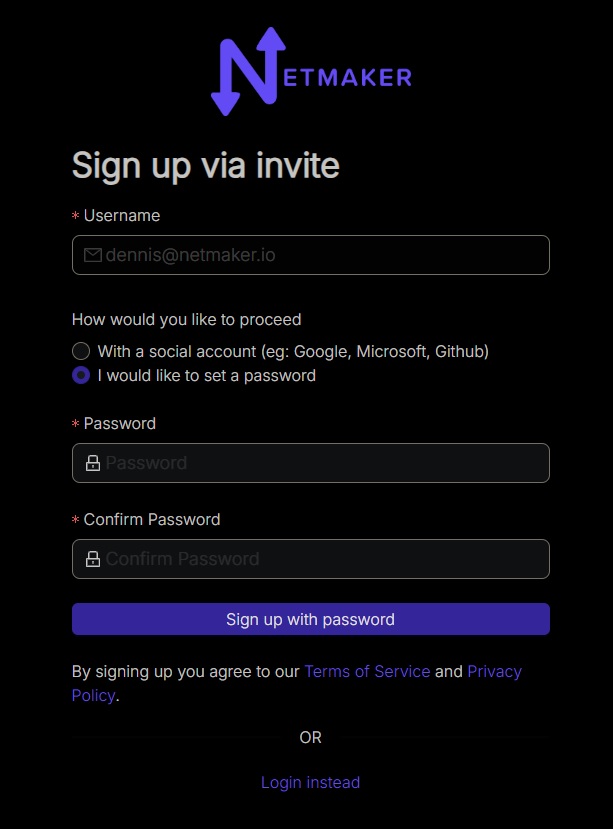
Letting users sign up by themselves (SSO/OAuth)
If OAuth is integrated on your Self-hosted Netmaker server, users can self-signup via RAC or web UI:
Example server domain: my-netmaker.my-org.com
Web UI: https://dashboard.my-netmaker.my-org.com
RAC Server field: api.my-netmaker.my-org.com (use your server domain as appropriate)
Once users sign up via OAuth/SSO, admins must approve and grant access:
Login as admin or superadmin.
Navigate to User Management → Pending Users.
Find the user and click Approve (confirm OK).
Go to Users tab, find the user and click their email.
Select Service User in Platform Access Level.
Under Additional Roles Per Network, for “my-org-vpn” select the Remote Access Gateway host.
Click Update User.

After approval, the user can login using RAC and access the assigned Remote Access Gateway/network.
Using RAC to Access a Server in a Remote Site Network
Service Users use Netmaker Desktop (RAC). They must specify the server to connect to:
Self-hosted: domain prefixed with api. (as given by the admin).
SaaS: Tenant ID (GUID) from Tenants table.

Example connection (demo server dentest.clustercat.com): authenticate with the invited user credentials or log in with OAuth/SSO as applicable. After logging in, the assigned Remote Access Gateway appears — click Connect.
If the RAGw has multiple endpoints, the endpoint chooser (›) allows selecting IPv4 vs IPv6 endpoint.
A WireGuard tunnel interface is created on the client. Traffic is routed: client → Remote Access Gateway (100.100.0.2) → Egress Gateway (100.100.0.3) → target server (e.g., 192.168.254.4).

Example: SSH to the remote server’s private IP over the tunnel works because application traffic is encapsulated within the WireGuard tunnel. Only UDP 51821 needs to be open on RAGw and Egress Gateway; no other ports need exposure for services in the remote LAN.

Hope you find this guide helpful and informational.
Links referenced
Integrating OAuth: https://docs.netmaker.io/docs/server-installation/integrating-oauth
Create Networks: https://docs.netmaker.io/docs/netmaker-network-setup-concepts/1-create-networks
Add Non-User Devices: https://docs.netmaker.io/docs/netmaker-network-setup-concepts/2-add-non-user-devices
Configuring a Remote Access Gateway: https://docs.netmaker.io/docs/features/remote-access-gateways-and-clients#configuring-a-remote-access-gateway
Remote Access Gateways and Clients: https://docs.netmaker.io/docs/features/remote-access-gateways-and-clients
Remote Access Client (RAC): https://docs.netmaker.io/docs/remote-access-client-rac
User Management: https://docs.netmaker.io/docs/features/user-management
Last updated
Was this helpful?