Building Zero-Trust Networks for Edge Devices with Netmaker

Edge devices are becoming critical components of modern infrastructure. From IoT sensors gathering data in remote locations to edge servers processing information closer to the source, these devices are transforming industries. However, this expansion of the network perimeter introduces significant security challenges. Traditional perimeter-based security models, which assume everything inside the network is trustworthy, are no longer sufficient. This is where the Zero-Trust security model becomes essential, especially for securing the vulnerable and often exposed edge.
How Netmaker Helps You Create a Zero Trust Network
Create a dedicated network
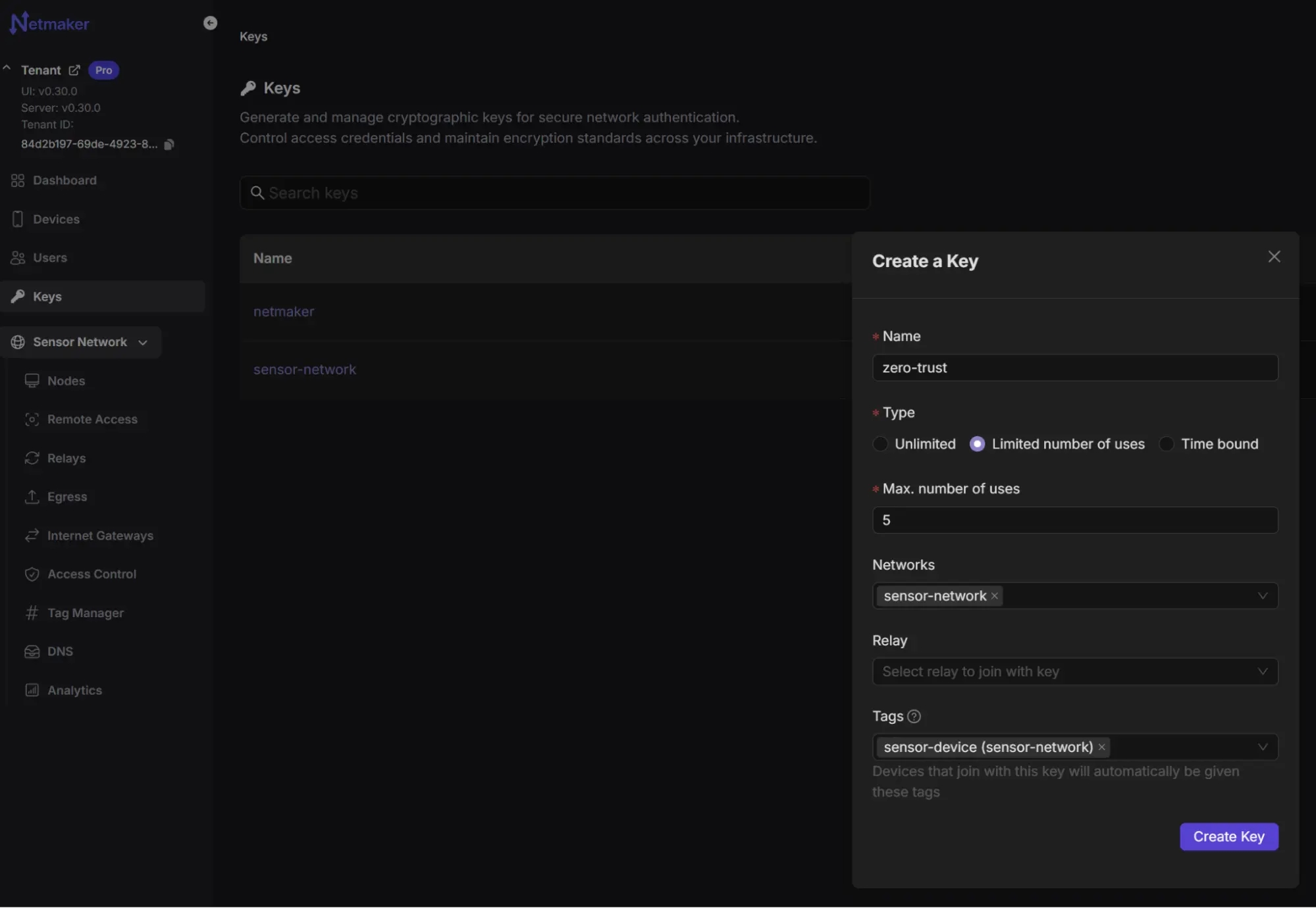
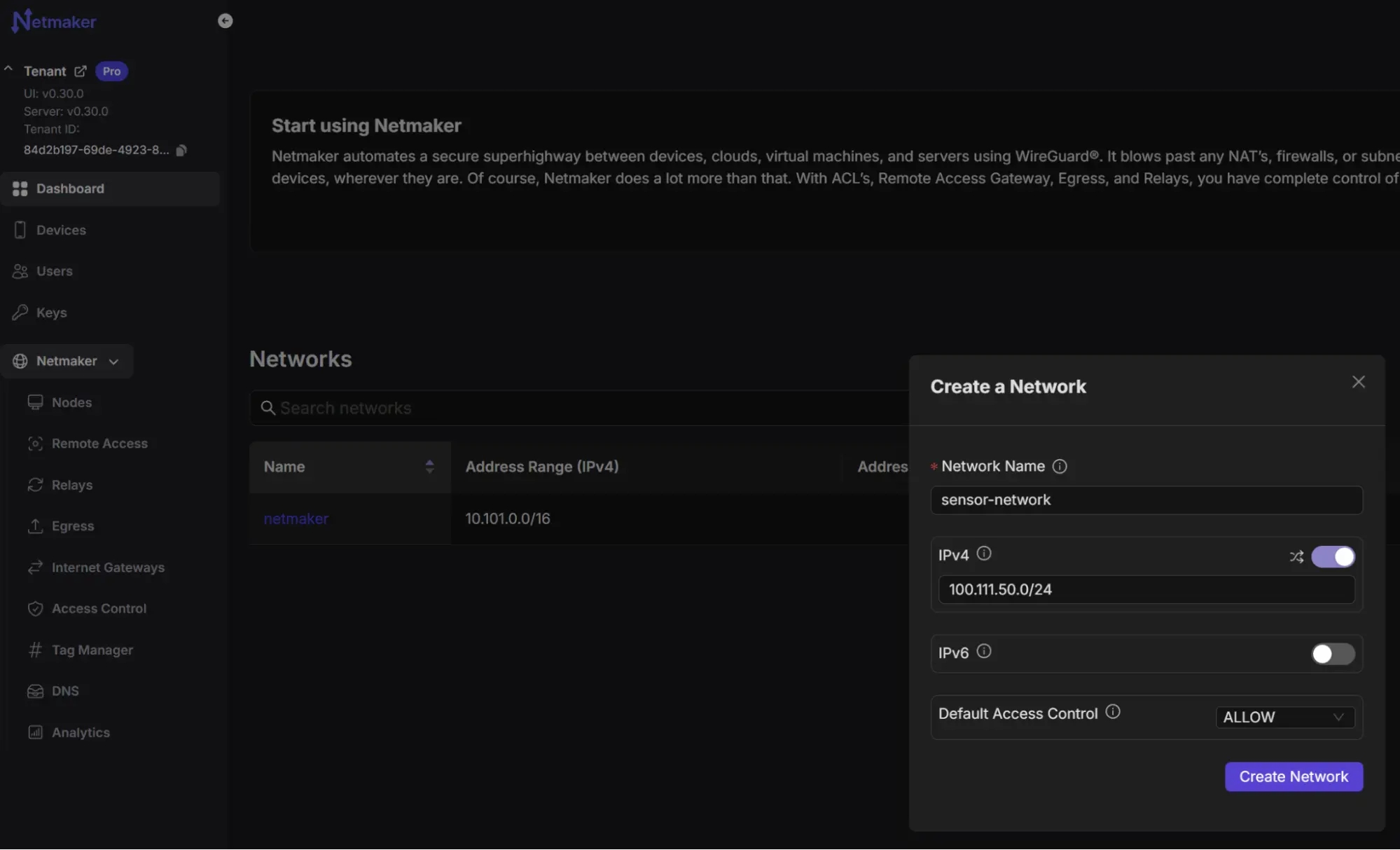
Imagine you’re deploying a fleet of sensors across 50 wind farms. You can use the Netmaker CLI (NMCTL) to automate the network setup or use the Netmaker Dashboard. First, create a dedicated network for your sensors:
Or use the command:
This creates a network named "sensor-network" with a private address range and a default deny policy, embodying the Zero-Trust principle of least privilege.
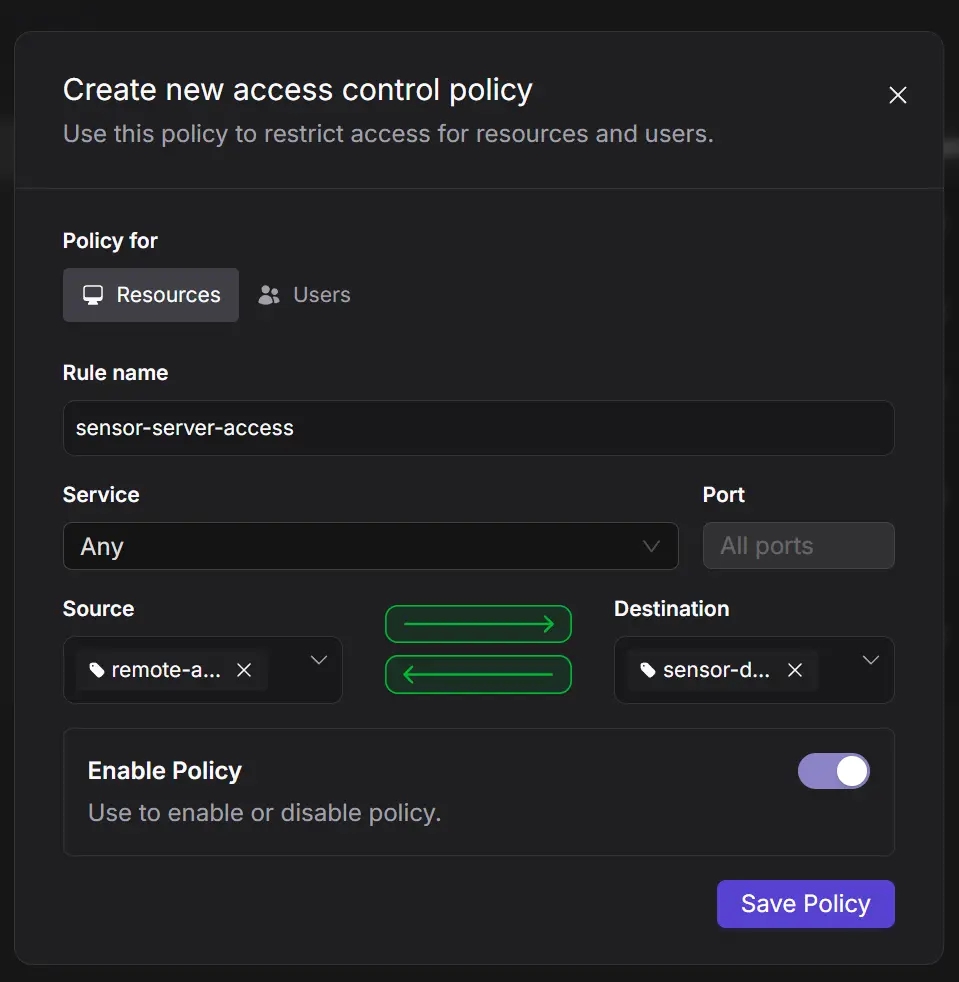
Define ACLs (Access Control Lists)
Define ACLs to restrict communication. For instance, allow your data aggregation server (node ID server-node-id) to communicate with the "sensor-device" tagged devices:
Or use the command:
This ensures that only your designated server can communicate with the sensor devices, preventing unauthorized access.
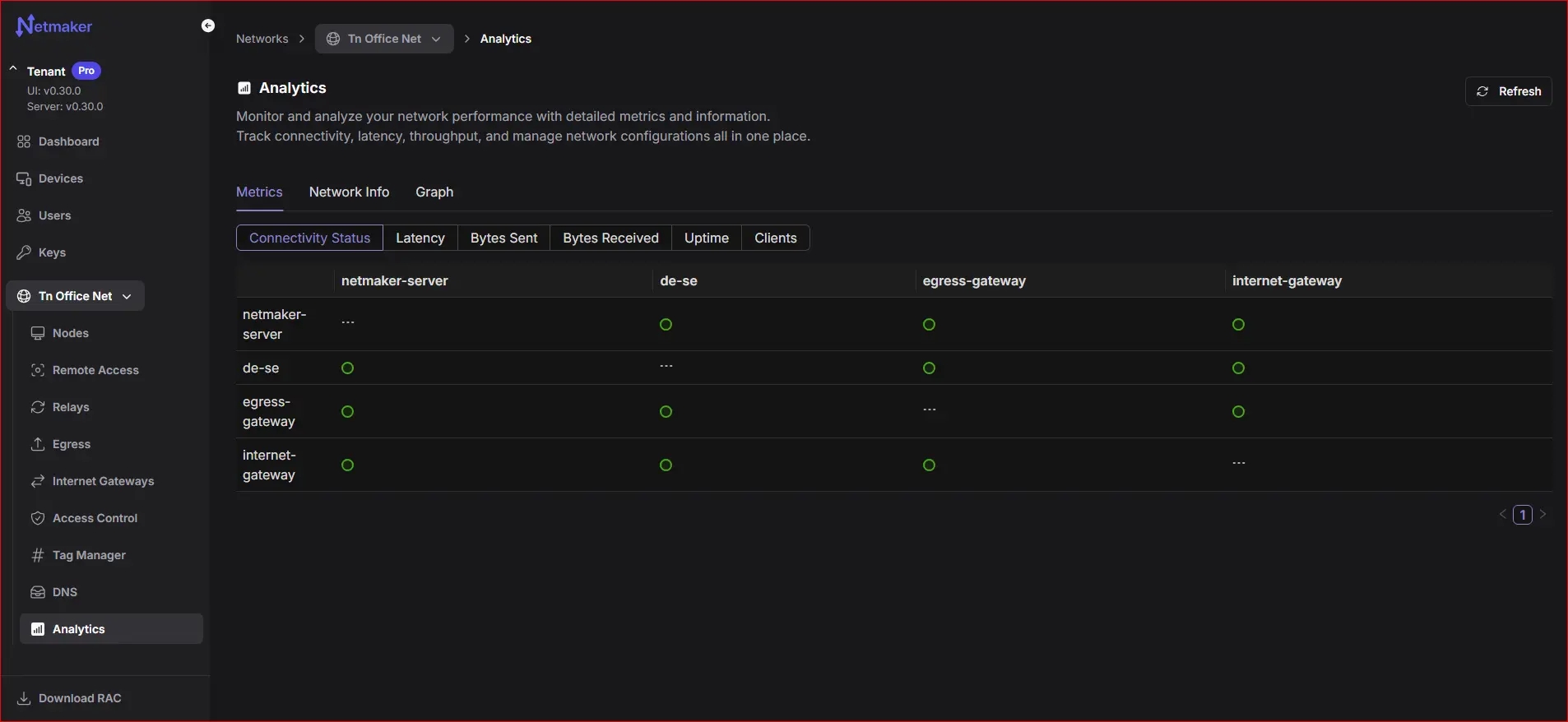
Monitor network performance
Monitor the network performance and connectivity using the Netmaker Metrics Dashboard, ensuring your Zero-Trust policies are effectively maintained over time:
Zero Trust
Zero-Trust is not a product, but a strategic approach to security that centers on the principle of "Never Trust, Always Verify." No user or device should be automatically trusted, regardless of location or network affiliation. Every access request must be authenticated, authorized, and continuously validated. This approach is crucial for edge devices, which are often deployed in less controlled environments and can be prime targets for malicious actors.
Netmaker, a platform for creating and managing virtual overlay networks using WireGuard, provides the foundation for implementing Zero-Trust principles in your edge device infrastructure. By leveraging Netmaker's flexible and secure networking capabilities, organizations can move beyond perimeter security and embrace a more robust security posture for distributed edge environments.
Network Segmentation
Network segmentation is a foundational pillar of Zero-Trust, and Netmaker supports it by letting you create separate, isolated networks. Segment edge devices by function, location, or security level to prevent lateral movement in case of a breach. You can create networks via the Netmaker dashboard, defining non-overlapping address ranges for isolation.
Granular Access Control
Netmaker's Access Control Lists (ACLs) provide precise control over communication between nodes. While Netmaker defaults to a full mesh network, in Zero-Trust you should prefer a "default deny" posture and explicitly allow required paths. Configure rules through the ACL interface in the UI. Netmaker Professional adds New ACLs (Pro) for policies based on users and resources for finer-grained access management.
User Management
Netmaker Professional offers robust User Management (Pro). Create service users for programmatic access and platform users for administrative tasks, each with tailored permissions. Use User Groups (Pro) to manage team permissions efficiently (for example, a "field technicians" group with limited diagnostic access). Netmaker supports OAuth integration so you can leverage existing identity providers for authentication.
Ensure only authorized devices join your Zero-Trust edge network using Netmaker's Enrollment Keys. Keys can have limited uses or expirations. For automated onboarding, use Tag Management (Pro) to group devices based on enrollment keys.
Continuous Monitoring
Continuous monitoring and visibility are essential to maintain Zero-Trust. Netmaker Professional's Analytics (Pro) offers insights into connectivity, latency, and data transfer. The Metrics (Pro) interface provides an overview of performance, and integration with Prometheus and Grafana enables advanced monitoring and alerting.
Netmaker for the Win
By combining network segmentation, granular access control, robust user management, and continuous monitoring, Netmaker enables you to build Zero-Trust networks for edge devices. This approach enhances security, simplifies management, and improves operational efficiency for distributed edge environments. Netmaker provides the speed, flexibility, and features required to implement this security paradigm, helping organizations secure edge deployments and reduce attack surfaces.
Last updated
Was this helpful?